Description
Holmes receives a breadcrumb from Dr. Nicole Vale – fragments from a string of cyber incidents across Cogwork-1. Each lead ends the same way: a digital calling card signed JM.
TL;DR
- First User-Agent:
Lilnunc/4A4D - SpecterEye(fromaccess.log, first request to/robots.txt) - Web shell filename:
temp_4A4D.php(fromaccess.log, request with?cmd=parameter in/uploads) - Exfiltrated database:
database_dump_4A4D.sql(fromaccess.log, file download entries) - Recurring string:
4A4D(seen in User-Agent strings and filenames) - Linked campaigns:
5(CTI platform, search IoC4A4D) - Tools & malware linked:
9(CTI platform, nodeJMconnections) - Malware SHA-256 hash:
7477c4f5e6d7c8b9a0f1e2d3c4b5a6f7e8d9c0b1a2f3e4d5c6b7a8f9e0d17477
(CTI platform, malware entry -> Links tab) - C2 IP address:
74.77.74.77(CogWork Security Platform, hash lookup -> View Details) - Persistence file created:
/opt/lilnunc/implant/4a4d_persistence.sh(CogWork Security Platform, file operations) - Open ports on TA server:
11(CogNet Scanner, scan of74.77.74.77) - Organization:
SenseShield MSP(CogNet Scanner, IP details view) - Cryptic banner (port 7477):
“He’s a ghost I carry, not to haunt me, but to hold me together – NULLINC REVENGE”
(CogNet Scanner, Services tab)
Solution
Three log files are attached to the challenge, access.log, application.log and waf.log. Let’s begin with the questions we have to answer.
Analyze the provided logs and identify what is the first User-Agent used by the attacker against Nicole Vale’s honeypot. (string)
The first entry in access.log shows entries originating from the same IP address, 121.36.37.224. Examining the first record, we can identify the initial User-Agent used in the attack.
2025-05-01 08:23:12 121.36.37.224 - - [01/May/2025:08:23:12 +0000] "GET /robots.txt HTTP/1.1" 200 847 "-" "Lilnunc/4A4D - SpecterEye"Answer: Lilnunc/4A4D - SpecterEye
It appears the threat actor deployed a web shell after bypassing the WAF. What is the file name? (filename.ext)
By further inspecting the access.log, we can find some entries that call a PHP script using the query parameter cmd, indicating this was the deployed web shell. Entry 34 shows the first call to the script.
2025-05-18 15:02:12 121.36.37.224 - - [18/May/2025:15:02:12 +0000] "GET /uploads/temp_4A4D.php?cmd=ls%20-la%20/var/www/html/uploads/ HTTP/1.1" 200 2048 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36"Answer: temp_4A4D.php
The threat actor also managed to exfiltrate some data. What is the name of the database that was exfiltrated? (filename.ext)
The last three entries in access.log show three file downloads.
2025-05-18 14:56:12 121.36.37.224 - - [18/May/2025:15:56:12 +0000] "GET /uploads/backup_2025_4A4D.tar.gz HTTP/1.1" 200 104857600 "-" "4A4D RetrieveR/1.0.0"
2025-05-18 14:58:23 121.36.37.224 - - [18/May/2025:15:58:23 +0000] "GET /uploads/database_dump_4A4D.sql HTTP/1.1" 200 52428800 "-" "4A4D RetrieveR/1.0.0"
2025-05-18 15:01:34 121.36.37.224 - - [18/May/2025:16:01:34 +0000] "GET /uploads/config_4A4D.json HTTP/1.1" 200 8192 "-" "4A4D RetrieveR/1.0.0"The second entry contains the name of the database dump.
Answer: database_dump_4A4D.sql
During the attack, a seemingly meaningless string seems to be recurring. Which one is it? (string)
As seen in access.log, both User-Agents and file names contain the string 4A4D.
2025-05-18 15:02:12 121.36.37.224 - - [18/May/2025:15:02:12 +0000] "GET /uploads/temp_4A4D.php?cmd=ls%20-la%20/var/www/html/uploads/ HTTP/1.1" 200 2048 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36"
2025-05-18 15:02:23 121.36.37.224 - - [18/May/2025:15:02:23 +0000] "GET /uploads/temp_4A4D.php?cmd=whoami HTTP/1.1" 200 256 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36"
2025-05-18 15:02:34 121.36.37.224 - - [18/May/2025:15:02:34 +0000] "GET /uploads/temp_4A4D.php?cmd=tar%20-czf%20/tmp/exfil_4A4D.tar.gz%20/var/www/html/config/%20/var/log/webapp/ HTTP/1.1" 200 128 "-" "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36"
2025-05-18 14:56:12 121.36.37.224 - - [18/May/2025:15:56:12 +0000] "GET /uploads/backup_2025_4A4D.tar.gz HTTP/1.1" 200 104857600 "-" "4A4D RetrieveR/1.0.0"
2025-05-18 14:58:23 121.36.37.224 - - [18/May/2025:15:58:23 +0000] "GET /uploads/database_dump_4A4D.sql HTTP/1.1" 200 52428800 "-" "4A4D RetrieveR/1.0.0"
2025-05-18 15:01:34 121.36.37.224 - - [18/May/2025:16:01:34 +0000] "GET /uploads/config_4A4D.json HTTP/1.1" 200 8192 "-" "4A4D RetrieveR/1.0.0"Answer: 4A4D
OmniYard-3 (formerly Scotland Yard) has granted you access to its CTI platform. Browse to the first IP:port address and count how many campaigns appear to be linked to the honeypot attack.
Browsing to the CTI platform, we can see a bunch of graphs.
By searching for the IoC 4A4D in the CTI platform, we can identify all the linked campaigns.
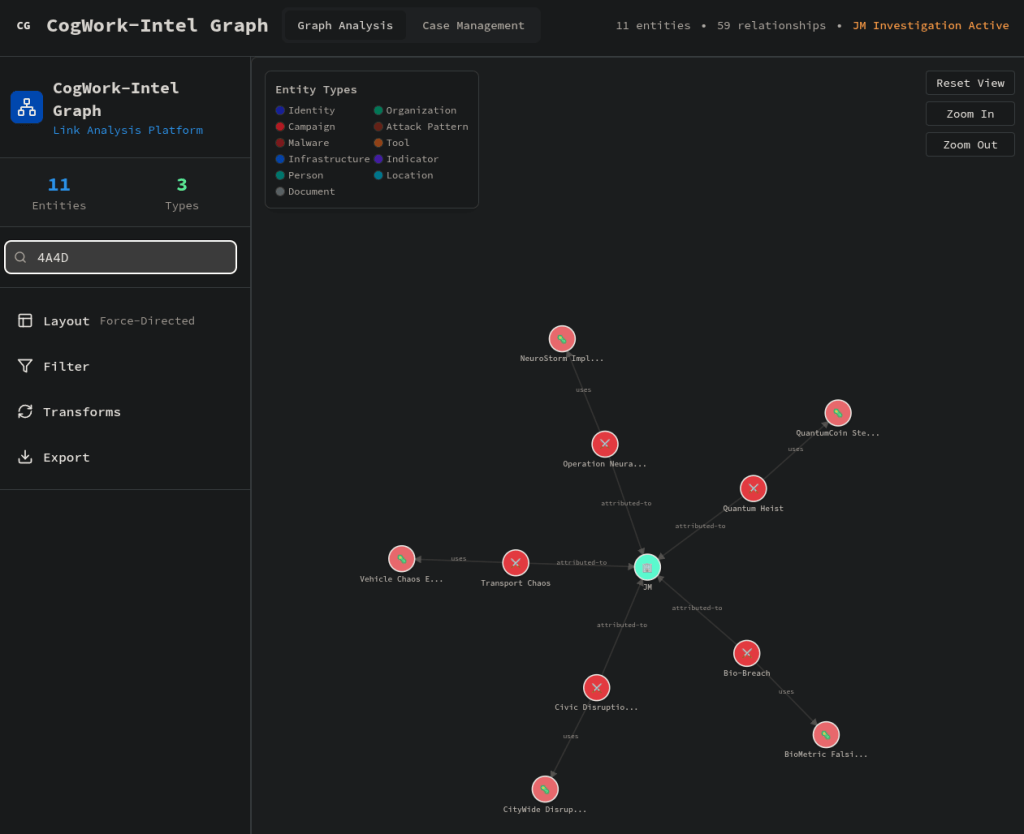
Answer: 5
How many tools and malware in total are linked to the previously identified campaigns? (number)
Looking at the node JM on the main graph, we can find all the malware and tools that are linked to those campaigns.

Answer: 9
It appears that the threat actor has always used the same malware in their campaigns. What is its SHA-256 hash? (sha-256 hash)
If we click on one of the malware entries, for example QuantumCoin Stealer, we get more information about the malware.

Checking the Links tab, we find a hash indicator.
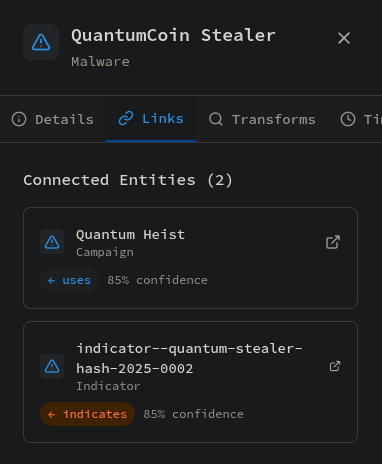
Clicking on the hash indicator shows the SHA256 hash.

Answer: 7477c4f5e6d7c8b9a0f1e2d3c4b5a6f7e8d9c0b1a2f3e4d5c6b7a8f9e0d17477
Browse to the second IP:port address and use the CogWork Security Platform to look for the hash and locate the IP address to which the malware connects. (Credentials: nvale/CogworkBurning!)
The second page is a hash lookup service. Using the previous hash as the search query shows information about the malware.
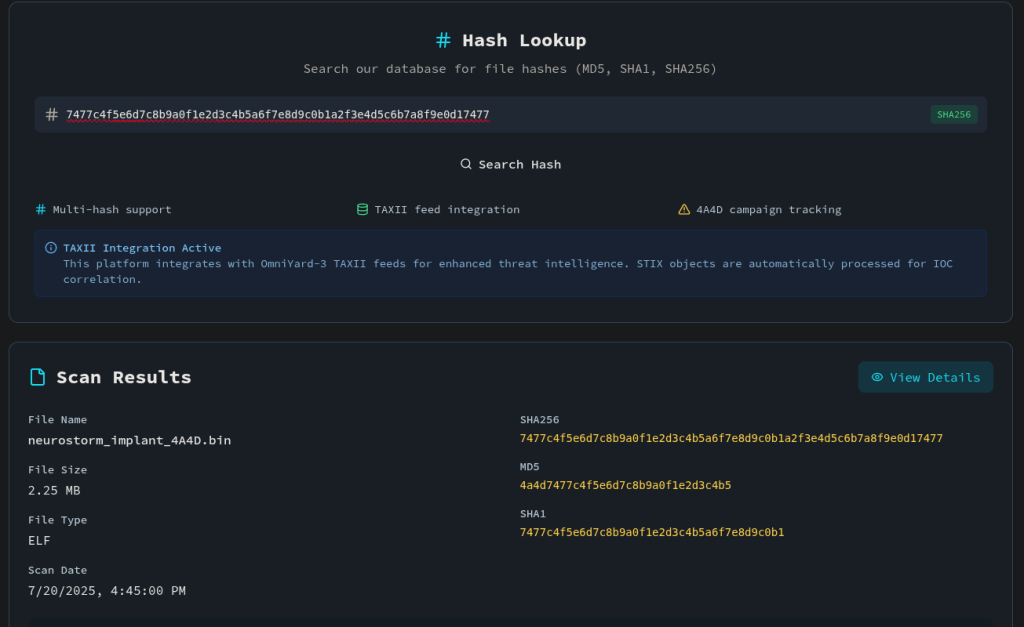
Clicking the “View Details” button returns even more information, including the C2 address.

Answer: 74.77.74.77
What is the full path of the file that the malware created to ensure its persistence on systems? (/path/filename.ext)
In the detailed analysis, the malware’s file operations are revealed, including the creation of a persistence script.
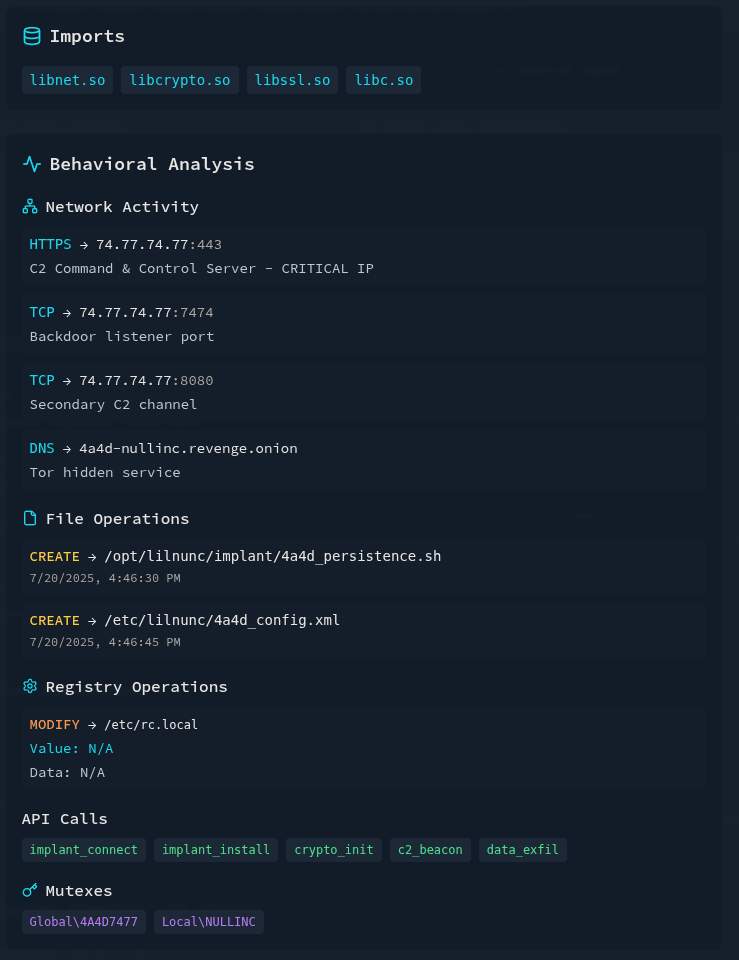
Answer: /opt/lilnunc/implant/4a4d_persistence.sh
Finally, browse to the third IP:port address and use the CogNet Scanner Platform to discover additional details about the TA’s infrastructure. How many open ports does the server have?
On the third page we can scan an IP address on CogNet. Searching for 74.77.74.77 returns information about the server, including open ports.

Answer: 11
Which organization does the previously identified IP belong to? (string)
Clicking the “Details” button returns more information about the IP. Here we find the name of the organization.
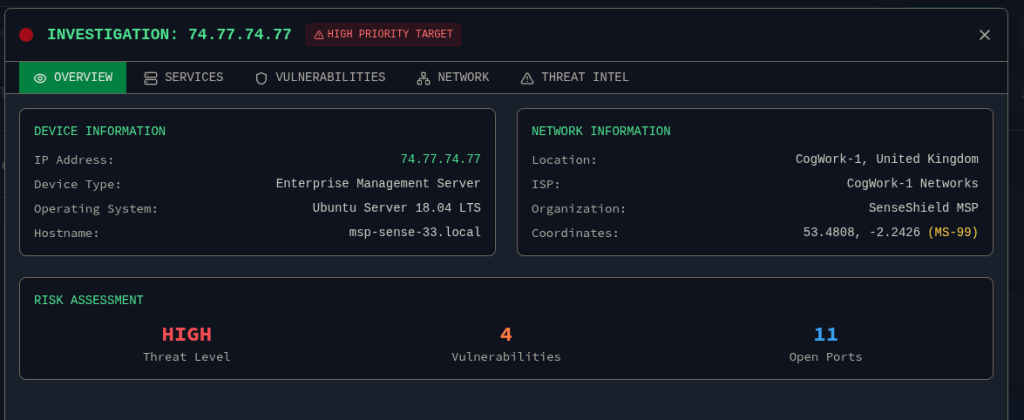
Answer: SenseShield MSP
One of the exposed services displays a banner containing a cryptic message. What is it? (string)
Switching tab to the “Services” tab shows banners from all the open ports. Scrolling through the list, we can find the cryptic message on port 7477.

Answer: He's a ghost I carry, not to haunt me, but to hold me together - NULLINC REVENGE
